How Effective is Your Vulnerability Management Program?
In this article:
- A vulnerability management program lays out the processes required for an IT security team to remediate security vulnerabilities within an organization’s network.
- An effective vulnerability management program should be continuous, intelligence-driven, and streamlined to enable teams to remediate as effectively as possible.
- Vulnerability management solutions like Prism Platform help organizations modernize their vulnerability management programs and improve remediation from start to finish.
What is a Vulnerability Management Program?
A vulnerability management program consists of the steps and processes required to resolve weaknesses in an organization’s network. A vulnerability management program should provide IT security teams with a framework for maintaining complete visibility and control of their organization’s security posture, so they can resolve issues as effectively and efficiently as possible. Ultimately, the goal of vulnerability management strategy is to minimize an organization’s attack surface and reduce risk.
What is the Vulnerability Management Process?
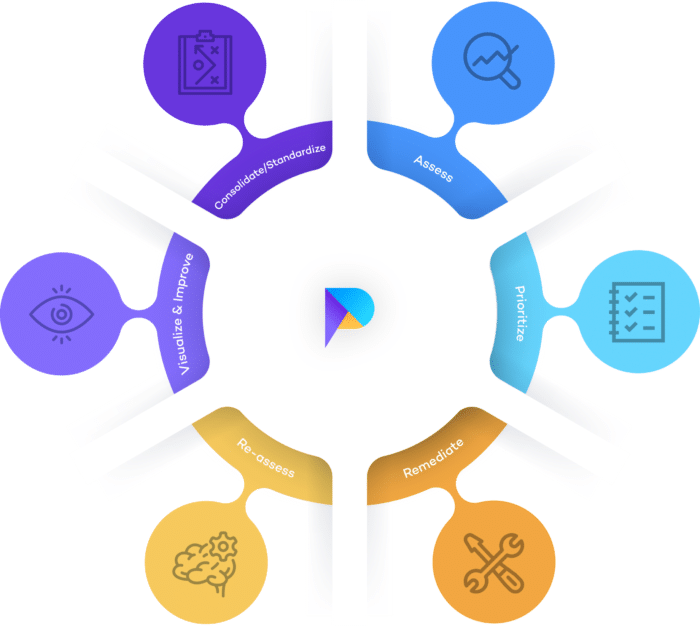
A vulnerability management program should start with the discovery of security issues, and conclude with validating whether remediation has been successful, before repeating continuously.
- Discover: Identify threats and vulnerabilities within your organization’s network by carrying out regular penetration tests and vulnerability scans.
- Consolidate: Centralize your threat and vulnerability assessment results in one place. Vulnerability management systems can make this process effortless.
- Assess: Analyse your security issues in line with cyber threat intelligence, such as exploit databases, to establish their severity, the likelihood that they will be exploited, and the impact they could have on your organization.
- Prioritize: Assign severity scores to your assets in line with your analysis, and other factors such as resource availability.
- Remediate: Carry out your threat and vulnerability management program to resolve vulnerabilities in line with your organization’s priorities.
- Re-assess: Verify whether your remediation efforts have been successful. Ultimately, your threat and vulnerability management remediation process should reduce business risk.
- Visualize and improve: Continuously improve your vulnerability management strategy; resolve any bottlenecks and ensure compliance with your organization’s service level agreements. For example, could you reduce your time-to-remediate (TTR)?
Best Practices for a Vulnerability Management Program Plan
A vulnerability management program plan should empower IT security teams to remediate as effectively and efficiently as possible. Consider these best practices when building a vulnerability management program.
Continuous
The time between security assessments is the time when your organization could be at risk. Threat and vulnerability management should be an ongoing process to close these gaps.
Intelligence-led
A vulnerability management program should be data-driven to ensure IT security teams can gain greater context of their issues, prioritize most effectively, and accurately evaluate risk.
Streamlined
Bottlenecks within a vulnerability management program can lose your team precious time. Processes and collaboration should be streamlined, empowering teams to address issues fast and efficiently.
Solutions for Vulnerability Management Programs
Solutions for vulnerability management programs could be software, platforms, or applications that make it easy for IT security teams to implement effective vulnerability management.
For example, a vulnerability management platform could aid prioritizing, delegating, reporting, tracking, and collaborating on remediation.
Prism Platform is our vendor-agnostic platform that helps you implement a modern vulnerability management program. Its powerful suite of features helps you improve remediation from start to finish.
Effective Vulnerability Management With Prism Platform

Here are just some of the ways Prism Platform makes it effortless to implement an effective vulnerability management program.
- Centralize security issues: Prism is vendor-agnostic, so you can use it to consolidate results from any vulnerability scanner or penetration testing vendor. Managing all your vulnerabilities in one place makes it seamless to continuously analyse, prioritize, and manage all issues across your estate.
- Intelligence-driven prioritization: Prism’s industry-leading Daily Exploit Detection alerts you to exploits for your issues on a daily basis, so you can gain the context needed to prioritize most effectively.
- Streamline remediation: Prism modernizes vulnerability management programs and makes it easy for teams to deliver fast and effective remediation, by reducing manual processes, integrating with ticketing systems, and much more.
- Real-time alerts: Prism ensures you have real-time insight into your threat landscape, by providing you with live updates from tests and continuous cyber threat intelligence alerts tailored to your digital estate. Read more on Continuous Vulnerability Management.
Threat Intelligence-led Vulnerability Management Program

Frequently Asked Questions About Vulnerability Management Programs
- Monthly remediation rate (the number of remediated issues versus outstanding issues)
- The number of exploitable issues within your estate (corroborated by intelligence feeds)
- The percentage change in the number of issues per month, for each severity score
- The number of outstanding issues within your estate shown over time. This can be expressed as a graph to reveal any trends.
- The age of outstanding security issues, broken down by severity level
- Mean-time-to-remediate (MTTR), broken down by severity level. This can also be expressed as a graph to show trends over time.
- The total number of: assets, assets with exploits, compliant assets, non-compliant assets (‘compliant’ with regards to your SLA deadlines)
- The number of outstanding issues per system owner. This can be expressed as a leader board to assist with following up on remediation
Prism Platform generates all these metrics for you, presented in clear Dashboards.
This strategy is particularly import for an enterprise vulnerability management program, where it is impossible for IT security teams to resolve every issue within a vast, global network.
A penetration test simulates a real-world attack on your organisation’s network, applications, systems, to identify any weaknesses. A pen test is conducted by skilled consultants, who use the same techniques as real-word hackers; you can think of it as ‘ethical hacking’. On the other hand, vulnerability scanning is carried out using automated tools and solely focuses on identifying vulnerabilities within software.
Cyber threat intelligence (CTI) enables your organisation to understand the potential threats and threat actors looking to perform malicious activities against your brand, employees, and customers. This intelligence can be gathered from a wide range of sources, including exploit databases, open source intelligence from the web, and more.
Within threat vulnerability management (TVM), the terms ‘vulnerability’, ‘risk’, and ‘threat’ are sometimes used interchangeably, but they have different meanings.
- Vulnerability: the security weaknesses within an organization’s IT network, e.g. a system misconfiguration
- Threat: incidents that could lead to a breach of an organization, e.g. insufficient phishing training for staff
- Risk: an evaluation of the impact a threat could have, specific to the organization, e.g. a critical asset is at risk
source https://www.rootshellsecurity.net/vulnerability-management-program/
Comments
Post a Comment