What is Cyber Security Risk Management?
As the number of threats to organizations continues to increase, so does cyber risk. That’s why Cyber Security Risk Management is an essential part of every organization’s IT security strategy.
Read on to learn more about Cyber Security Risk Management and how solutions like Prism Platform can help.
What is Cyber Risk?
Cyber risk is the likelihood of an organization falling victim to a cyber attack or internal cybersecurity threat, such as a data breach caused by human error.
Cyber risk considers the probability that an incident could occur and evaluates the impact this incident could have on an organization. This can be summarized as:
Risk = Probability x Impact
The probability of cyber risk can be broken down into vulnerabilities and threats.
Risk = (Vulnerabilities x Threats) x Impact
Vulnerabilities are security issues that exist within an organization’s digital landscape that could facilitate a cyber attack if left unresolved. Threats can be defined as the tactics, techniques, and procedures (TTPs) utilized by threat actors to commit malicious acts, such as deploying malware or sending phishing emails, as well as internal threats, like human error.
It is a combination of vulnerabilities and threats that inform the probability of risk to your organization.
The level of cyber risk is specific to an organization’s digital ecosystem and personnel. For example, a software containing a security vulnerability may pose a high cyber risk to Organization A but a low cyber risk to Organization B, if Organization A stores valuable information in this software, whereas Organization B does not.
What is Cyber Security Risk Management?
Cyber risk management is the process of identifying, analysing, prioritizing, and mitigating the risks to an organization.
The goal of cyber security risk management is to reduce the likelihood of risk and the impact of these risks if they were to materialize. This is critical to protecting an organization’s data, personnel, finances, and reputation.
As it’s impossible to address every risk in an organization’s digital ecosystem, risk management for cyber security helps organizations prioritize risk and focus on what’s most important.
For example, a cyber security risk management plan can help businesses answer questions like “do I need to patch this system?”, and if so, “how quickly should I patch this system?”.
As well as helping to prioritize, an effective cyber security risk management strategy can help teams continuously evaluate the success of their efforts and ensure they remain aligned with their organization’s goals.
How to Perform a Cyber Security Risk Assessment
A Cyber Security Risk Assessment underpins the processes involved to successfully execute Cyber Security Risk Management. The following steps outline this process, from identifying assets to continuous improvement.
1. Identify and prioritize assets
The first step in a cyber security risk assessment is to identify and prioritize your organization’s assets. This could include devices, software, servers, and many more. How you determine which assets are most important is specific to your organization. In general terms, an important asset could be defined as any asset that serves mission-critical processes, contains sensitive data, or is internet-facing, as these represent a vulnerable area of your organization’s attack surface.
2. Identify the threats to your organization
The next step is to consider the threats to your most important assets. These could be external threats, such as the deployment of malware by a cyber attacker, or internal threats, such as an employee accidentally leaking sensitive data. Once you have identified the threats to your assets, each asset can be assigned a threat level depending on how susceptible it is to these threats. These threat levels can guide your next steps.
3. Analyse the impact of these threats
Now it’s time to consider the impact of these threats, prioritizing the threats that would have the most severe consequences. If you have an effective vulnerability management solution, then a software vulnerability may not pose as much of a threat as, say, a phishing email, if your employees have not received quality training. By contextualizing the severity of threats inline with your organization’s cyber security strategy, you can pinpoint exactly where resources should be allocated to mitigate risk.
4. Implement controls to mitigate risk
The next step is to put controls in place to address the threats prioritized in step 3. ‘Controls’ refers to a broad range of processes and technologies that safeguard an organization and reduce risk.
Some of these controls might be:
- Continuous Vulnerability Management. This can be successfully implemented using a Vulnerability Management System.
- Continuous Security Testing, e.g. penetration tests and vulnerability scans
- Access Control Management
- Employee Security Awareness Training, e.g. phishing training
- Malware Defenses
The Centre For Internet Security (CIS) provides a comprehensive list of critical security controls.
5. Implement and measure your Cyber Security Risk Management process
Once you have defined which threats to prioritize, based on your critical assets, and therefore which controls to implement, you can ensure these controls are rolled out effectively to reduce organizational risk. Your Cyber Security Risk Management strategy should be a continuous process, as your threat landscape is ever-evolving. It is also important to evaluate the success of your strategy and make improvements on an ongoing basis, such as ensuring controls are matched to your latest threats to check coverage and identify any gaps.
Prism Platform and Cyber Security Risk Management

Prism Platform is a next generation vulnerability management solution that modernizes IT security teams. Its powerful suite of features helps organizations improve remediation from start to finish, including managing and mitigating cyber risk.
Global Overview
Prism enables you to visualize your global threat landscape in real-time, making it effortless to continuously analyse your technical risk.
Automated Exploit Detection
Prism’s industry-leading Daily Exploit Detection alerts you as soon as an exploit becomes available for an issue within your digital estate.
Insights and Reports
Prism’s Dashboards put key insights front-and-centre, such as the number of exploitable issues, and automates reporting.
Effective Remediation
Prism modernizes vulnerability management programmes and improves every aspect of remediation, helping teams resolve issues faster than ever before.
Asset Prioritization
Assign priority ratings to your assets, track the remediation status of associated vulnerabilities, and measure the success of the system owners assigned to them.
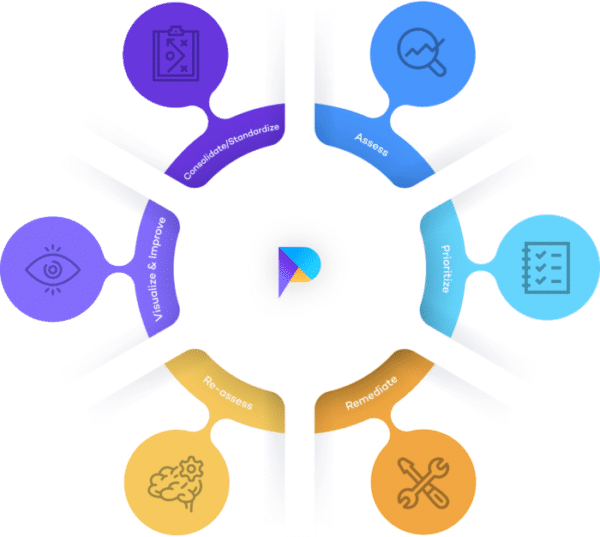
We have aligned Prism Platform with the Gartner® Vulnerability Management Cycle to ensure that best practice processes guide your remediation programmes.
source https://www.rootshellsecurity.net/cyber-security-risk-management/
Comments
Post a Comment