Risk Based Vulnerability Management
It’s impossible to address every cyber security risk within an organization’s threat landscape – there could be hundreds. That’s why Risk Based Vulnerability Management is becoming increasingly important to modern IT security strategy.
Read on to learn more about Risk Based Vulnerability Management and how solutions like Prism Platform can help.
What is Risk Based Vulnerability Management?
Risk Based Vulnerability Management helps organizations focus their remediation efforts on the vulnerabilities that pose the most risk.
A risk-based vulnerability management strategy helps IT security teams determine the likelihood of a vulnerability being exploited, in line with the importance of the asset that would be impacted.
For example, Risk Based Vulnerability Management can help businesses answer questions like “do I need to patch this system?”, and if so, “how quickly should I patch this system?”.
As well as helping organizations effectively prioritize remediation, risk based vulnerability management helps organizations allocate their resources most effectively, ensuring that money is not spent on risks that are unlikely to have an impact.
Prism reduces MTTR for exploitable issues by 61%
Risk Based Vulnerability Management Best Practices
Before a risk based vulnerability management strategy can be successfully implemented, organizations should carry out a carry out a cyber security risk assessment, so their risk appetite is clearly defined.
1. Identify and prioritize assets
Clearly defining your risk appetite is essential to effective risk based vulnerability management. The first step is to make a comprehensive inventory list of your assets, and then prioritize them. Generally, important assets could be any that are business-critical, internet-facing, or contain sensitive data, but this will be specific to your organization.
2. Be Led by Threat Intelligence
Risk based vulnerability management should be intelligence-led. This enables teams to accurately evaluate vulnerabilities based on real-world context. One way of doing this is by integrating exploit resources, such as Exploit DB or Zero Day Initiatives, with your processes.
3. Maximize Network Visibility
You can’t accurately prioritize your vulnerabilities with incomplete data. It’s essential that you have visibility of as much as your network as possible. Up-to-date asset inventories and consolidating your vulnerability data into one database are some of the ways you can ensure you are basing your decisions on the complete picture.
Prism users are able to track 87% more assets than before using the platform
Prism Platform and Risk Based Vulnerability Management

Prism Platform is a next generation vulnerability management solution that modernizes IT security teams. Its powerful suite of features helps organizations improve remediation from start to finish, including managing and mitigating cyber risk.
Global Overview
Prism enables you to visualize your global threat landscape in real-time, making it effortless to continuously analyse your technical risk. Prism users are able to track 87% more assets than before using the platform.
Automated Threat Intelligence
Prism makes it easy to ensure intelligence drives your risk based vulnerability management program. Prism’s industry-leading Daily Exploit Detection alerts you as soon as an exploit becomes available for an issue within your digital estate.
Insights and Reports
Prism’s dashboards put key insights front-and-centre, such as the number of exploitable issues, so you are continuously aware of the status of your risk based vulnerability strategy.
Effective Remediation
Prism modernizes vulnerability management programmes and improves every aspect of remediation, helping teams resolve issues faster than ever before. Prism reduces mean-time-to-remediate for exploitable issues by 61%.
Asset Prioritization
Assign priority ratings to your assets, track the remediation status of associated vulnerabilities, and measure the success of the system owners assigned to them.
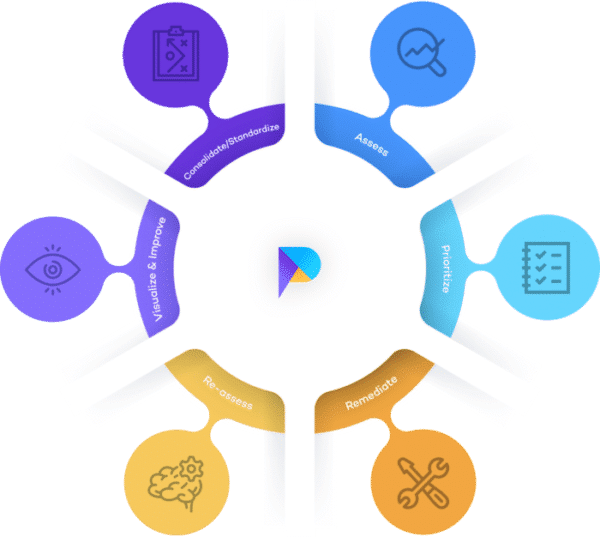
We have aligned Prism Platform with the Gartner® Vulnerability Management Cycle to ensure that best practice processes guide your remediation programmes.
source https://www.rootshellsecurity.net/risk-based-vulnerability-management/
Comments
Post a Comment