The Fortinet FortiClient VPN Bug That Isn’t
Once upon a time, vendors would be grateful for bug hunters reporting flaws in their software so they could fix them.
With their more detailed understanding of the software in question (i.e. possession of source code), they can easily locate the issues from a contextual explanation and put a fix in place with minimal effort.
To accept an issue as valid, Fortinet require a proof-of-concept to be constructed.
Sadly, without the source code, or a completely functioning Fortinet VPN solution (with DNS split tunnelling) to deconstruct, Rootshell are unable to construct such code, and it is not possible to create a proof-of-concept.
Background on the Fortinet Issue
The Rootshell team discovered a bug within Fortinet’s FortiClient VPN.
The issue relates to invalid parsing of the DNS responses received over the tunnel in the kernel driver fortitransctrl.sys.
A classic infinite loop exists in the parsing of DNS compression pointers, much like the old instances of ipv6 option parsing (CVE-2007-3157), wherein the offset/length is not checked for a zero value, and no iteration count is maintained and bounded.
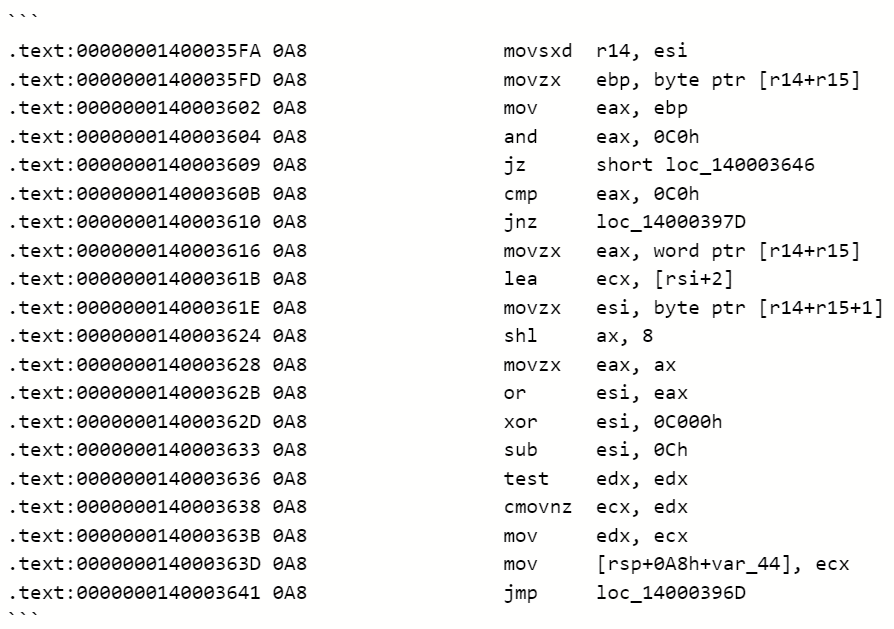
In the disassembly above, the register esi, r15 contains the current offset and the pointer to the DNS response in memory respectively. Note that the value of esi computed at offset 140003633 is not checked for zero.
This facilitates an infinite loop in the parsing routine, should a DNS response be received with a compression pointer value A=’C0NN’, where NN is a value such that NN-12 bytes is the offset in the DNS response at which A is located.
source https://www.rootshellsecurity.net/the-fortinet-forticlient-vpn-bug-that-isnt/
Comments
Post a Comment