Hacking a Tesla port with the Flipper Zero
Author: Paul Cronin (Partner and Co-Founder)
Software Defined Radio (SDR) is not a new subject, however the release of the Flipper Zero has recaptured my interest in the subject.
I don’t currently own a Flipper Zero, but it looks like a Swiss army knife for Radio Frequency (RF) manipulation supporting Sub-1 GHZ range with integrated 433MHZ, 125MHZ RFID, NFC, Bluetooth, Infrared and the ability to connect it to hardware with a SPI/UART to USB convertor for hardware hacking.

This little device, in my opinion, has made SDR more accessible to people who may not have explored this area before; getting some of this kit to work used to take lot of time and effort. It reminds me of when the first Penetration Testing distributions were released (Like Backtrack now known as KALI) which allowed people to play with tools that would have previously taken some skills to get working and compiled.
As mentioned Software Defined Radio is not new and the Hack-RF one from Great Scott Gadgets has been available for many years and is capable of receiving and transmitting on a frequency range of 1 MHz to 6 GHz with maximum output power of up to 15 dBm depending on the band.
Wanting to get playing with SDR again, and after much consideration, I decided to purchase a Chinese clone of the Hack-RF from Aliexpress called the Portapack, rather than a Flipper Zero.
The PortaPack is as it sounds a portable way to run the HackRF One without needing a computer. I’ve got other devices that can inspect RFID and broadcast IR, Bluetooth etc. so decided to get one of these devices.
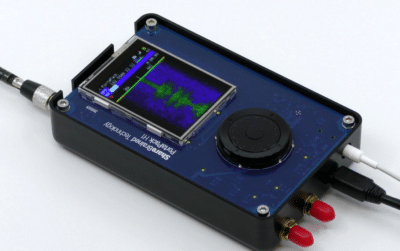
The device also comes shipped with a custom Firmware called “Mayhem” and as judging by the description could get you in a lot of trouble… Modules like signal Jamming and numerous transmit modes could land you in hot water depending on your country’s laws. Since this activity would be illegal in the UK, and me not wanting to accessorise with matching wrist bracelets, I won’t be exploring at these features.
What I have been experimenting with is the ability for the Portapack to capture and replay ISM band remote controls easily to an in-built SD card.
The last time I played around with SDR I managed to upset my wife. Back in 2015 she leased a Range Rover Evoque, which had a wireless key. So no key in the ignition push start (Common today) Whilst waiting to pick up my son from school and me being board.
I decided to see what would happen if I cloned the keyfob and broadcast the signal back to the car. Well I know most modern cars should be using rolling codes and the Range Rover does, but it sent the car into a bit of a confused state and it refused to start. I’m pretty sure I upset the KVM (Keyless Vehicle Module) that is used in Jaguar/Land Rover cars. Thankfully, after disconnecting the battery and re-connecting it the car sprang back into life and started. My wife read me the riot act and told me to leave our stuff alone.
Well I ignored all of that, as she now owns a Tesla Model 3 and I have a new SDR toy to play with.
The charging port on Tesla electric vehicles is protected via a cover that can be opened by charging stations via a wireless signal transmitted at 315 MHz in the US & 433MHZ in the UK. It turns out that the command to open the port is totally without any security. This makes it possible to record or recreate the signal, and play it back anywhere using a transmit capable SDR device like a PortaPack or Flipper one.
The level of damage a malicious party could cause through the charging port is limited and this does not give you any access to the inside of the vehicle but it is amusing to see especially as it works from quite a distance and is not unique to any particular Tesla. Well, maybe not that amusing to my wife, who watched with trepidation as I stood on our driveway messing with her car, again.
A Few years ago my colleague Shaun found that his 2012 Kia Sportage did not support rolling codes. Simply capturing the car key fob and replaying it would unlock that vehicle. After contacting KIA to report the issue they “fobbed” him off (pun intended) explaining that they do use rolling codes and that there is no issue, presumably attempting some sort of Jedi mind trick on Shaun (these are not the codes you’re looking for).
He also contacted Thatcham who provide all of the UK vehicle security assessments established by the UK motor insurance industry. They were more interested but not that concerned. If I recall the IT security company based in the US who we were both working for at the time were worried about KIA suing us so we were asked to not make a big deal out of it.
Rolling on into 2022 (see what I did there) and CVE-2022-27254 was discovered by some university student researchers that the wireless locking on a large number of Honda vehicles was vulnerable to simple RF replay attacks. In addition a vulnerability identified by twitter user @kevin2600 affects ALL Honda vehicles currently on the market (2012-2022). The vulnerability is dubbed ‘Rolling-PWN‘ and as the name suggests, details a method for defeating the rolling code security that exists on most Honda vehicles.
After each key fob button press the rolling codes synchronizing counter is increased. However, the vehicle receiver will accept a sliding window of codes by design, to avoid accidental key presses. By sending the commands in a consecutive sequence to the Honda vehicles, it will resynchronize the counter. Once the counter is resynced, commands from the previous cycle of the counter worked again. These commands can be used later to unlock the car at will.
The vulnerability has been tested on various Honda vehicles with HackRF SDRs, and this seems to indicate that all Honda vehicles since 2012 are vulnerable to RF signal replay for door-open, door-close, boot-open and remote start (If applicable).
Fortunately for me, my Mother-in-law (who lives next door) owns a Honda Jazz so I was able to test this out and it works!
Prevention
Manufacturers must always implement Rolling Codes, otherwise known as hopping code. It is a security technology commonly used to provide a fresh code for each authentication of a remote keyless entry (RKE) or passive keyless entry (PKE) system.
Use the PKE as opposed to the RKE, this would make it significantly harder for an attacker to clone/read the signal due to the proximity they would need to be at to do so.
Vehicle Owners
A Bengal Tiger locked in the car would be my advice, but if you don’t have one to hand maybe a good quality steering lock to slow any thieves down. My plan is to do some of my own research into some other makes of vehicle both in RF and looking into the Can bus technology used in some of these vehicles as I like messing about with cars and IT.
source https://www.rootshellsecurity.net/hacking-a-tesla-port-with-the-flipper-zero/
Comments
Post a Comment