How to Carry Out a Vulnerability Assessment
Vulnerability assessments identify security issues within a digital infrastructure, which is essential for helping organizations defend against attacks. Read on for how vulnerability assessments can be executed, as well as how a vulnerability assessment management solution can help.
What is a Vulnerability Assessment?
A vulnerability assessment identifies security issues within an organization’s networks, systems, and applications.
Vulnerability assessments typically consist of automated vulnerability scans to analyse a network for vulnerabilities. A manual penetration test may also be recommended alongside a vulnerability scan to establish whether the vulnerabilities could be exploited, and what impact this could have on the organization.
What is the purpose of a vulnerability assessment?
The purpose of a vulnerability assessment is to provide organizations with insight into the weaknesses that exist within their estates, so that appropriate prioritization and remediation can be carried out before a vulnerability can be exploited.
Why are Vulnerability Assessments Important?
Vulnerability assessments are critical components of any organization’s cyber security strategy.
New vulnerabilities are emerging all the time and threat actors continuously evolve their tactics. If a threat actor accesses your network via a vulnerability, they could cause serious damage, such as steal sensitive data or launch a Denial of Service (DoS) attack.
Vulnerability assessments ensure organizations are prepared for real-world attacks and enable them to effectively remediate risk.
How is a Vulnerability Assessment Carried Out?
There is no singular definition for a ‘vulnerability assessment’; some providers may recommend a vulnerability scanning solution, whereas others may suggest a penetration test. An effective approach to vulnerability assessments would be a combination of both, followed by continuous vulnerability management.
1. Vulnerability Scanning
Vulnerability scanning leverages automated tools to scan for security vulnerabilities within a network. By scanning on a regular basis, you can put your organization in the strongest position to identify and eliminate threats before they can be exploited by cyber criminals.
2. Penetration Testing
Penetration testing services utilize a range of manual techniques to assess an organization’s networks, systems, and applications for security weaknesses. The tester will attempt to safely exploit vulnerabilities to determine whether they could enable an attack.
3. Continuous Vulnerability Management
A vulnerability management program provides IT security teams with a framework for maintaining complete visibility and control of their organization’s security posture. Vulnerability management should be continuous to ensure your vulnerability assessments can be actioned as effectively and efficiently as possible. A vulnerability management platform like Prism can make this effortless.
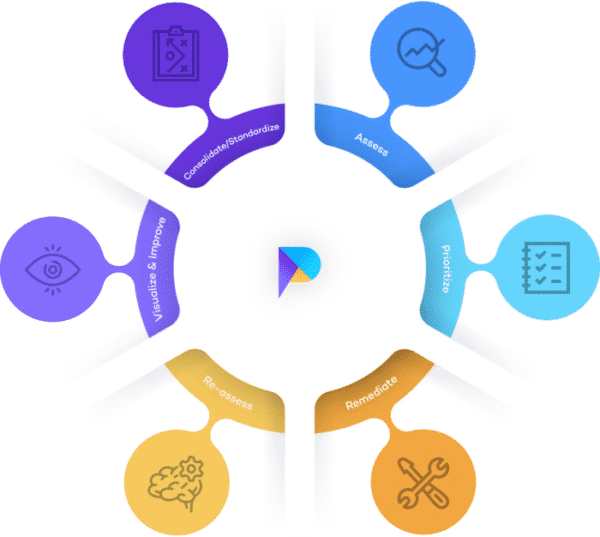
Vulnerability Assessment Solutions
A vulnerability assessment solution enables you to manage issues from different types of security assessments in one place. Vendor neutral tools make it easy to consolidate testing from different cyber vulnerability assessment providers.
As well as centralizing your vulnerabilities, a vulnerability assessment tool helps teams prioritize, delegate, report, track, and collaborate on the remediation of vulnerabilities.
Prism Platform is our vendor neutral platform that helps you implement modern and effective vulnerability management programs, reducing mean-time-to-remediate by up to 61%.
Manage Vulnerability Assessments with Prism Platform

Here are just some of the ways Prism Platform makes it effortless to manage vulnerability assessments.
- Centralize security issues: You can use Prism to consolidate results from any vulnerability scanner or penetration testing vendor. Managing all your vulnerability assessment results in one place makes it seamless to continuously analyse, prioritize, and remediate.
- Intelligence-driven prioritization: Prism’s industry-leading Daily Exploit Detection and Active Exploit Detection alerts you to exploits for your issues on a daily basis, so you can gain the context needed to prioritize most effectively.
- Streamline remediation: Prism modernizes vulnerability management programs and makes it easy for teams to deliver fast and effective remediation, by reducing manual processes, integrating with ticketing systems, and much more.
- Real-time alerts: Prism ensures you have real-time insight into your threat landscape, by providing you with live updates from tests and continuous cyber threat intelligence alerts tailored to your digital estate.
Frequently Asked Questions about Vulnerability Assessments
Vulnerability scans continuously assess different components of an organization’s network for security weaknesses, such as firewalls, web applications, and server vulnerability testing.
The scans provide exhaustive lists of vulnerabilities identified. It is then up to security teams to determine which issues require remediation.
Penetration testing is a manual cyber security test that assesses an organization’s networks, systems, and applications for security weaknesses. Also known as ‘pen testing’ or ‘ethical hacking’, a pen tester attempts to safely exploit vulnerabilities to determine whether they could enable an attack.
Some people consider a ‘vulnerability assessment’ to be the same as a vulnerability scan. In this case, the difference is that a vulnerability scan is carried out using automated tools and solely focuses on identifying vulnerabilities within software. Whereas a penetration test is a manual assessment that attempts to exploit vulnerabilities to establish how an organization could be hacked.
- Prepare for a real-world attack: Vulnerability assessments are one of the most effective ways to evaluate your security posture. By emulating the same tactics, techniques, and procedures used by sophisticated threat actors, vulnerability assessments truly put your organisation’s defences to the test.
- Uncover critical vulnerabilities: As the risk of cyber attacks continues to increase, it’s crucial you have complete visibility of your organisation’s vulnerabilities. Vulnerability assessments will identify any vulnerabilities, from low to high risk, so you can take action.
- Effectively remediate risk: Vulnerability assessments provide you with the data you need to manage and resolve vulnerabilities.
source https://www.rootshellsecurity.net/vulnerability-assessment/
Comments
Post a Comment